Examples and Demonstrations
When we use the phrase "Cyber Range", all we are referring to is a network environment that is deployed for the specific purpose of training, research, or what ever use case you require. An added benefit is with the Georgia Cyber Range, is that we provide tenant isolation between the projects where the various Cyber Ranges are hosted.
We can go beyond just simulation for a majority of environments due to the ecosystem of open source projects that we leverage. System and applications deployed within our Cyber Ranges are deployed and built in the same manor as they are in production environments hosted on AWS, Azure, Google Cloud, and traditional enterprise data centers.
What does a Cyber Range consist of?
It consists of the following components:
-
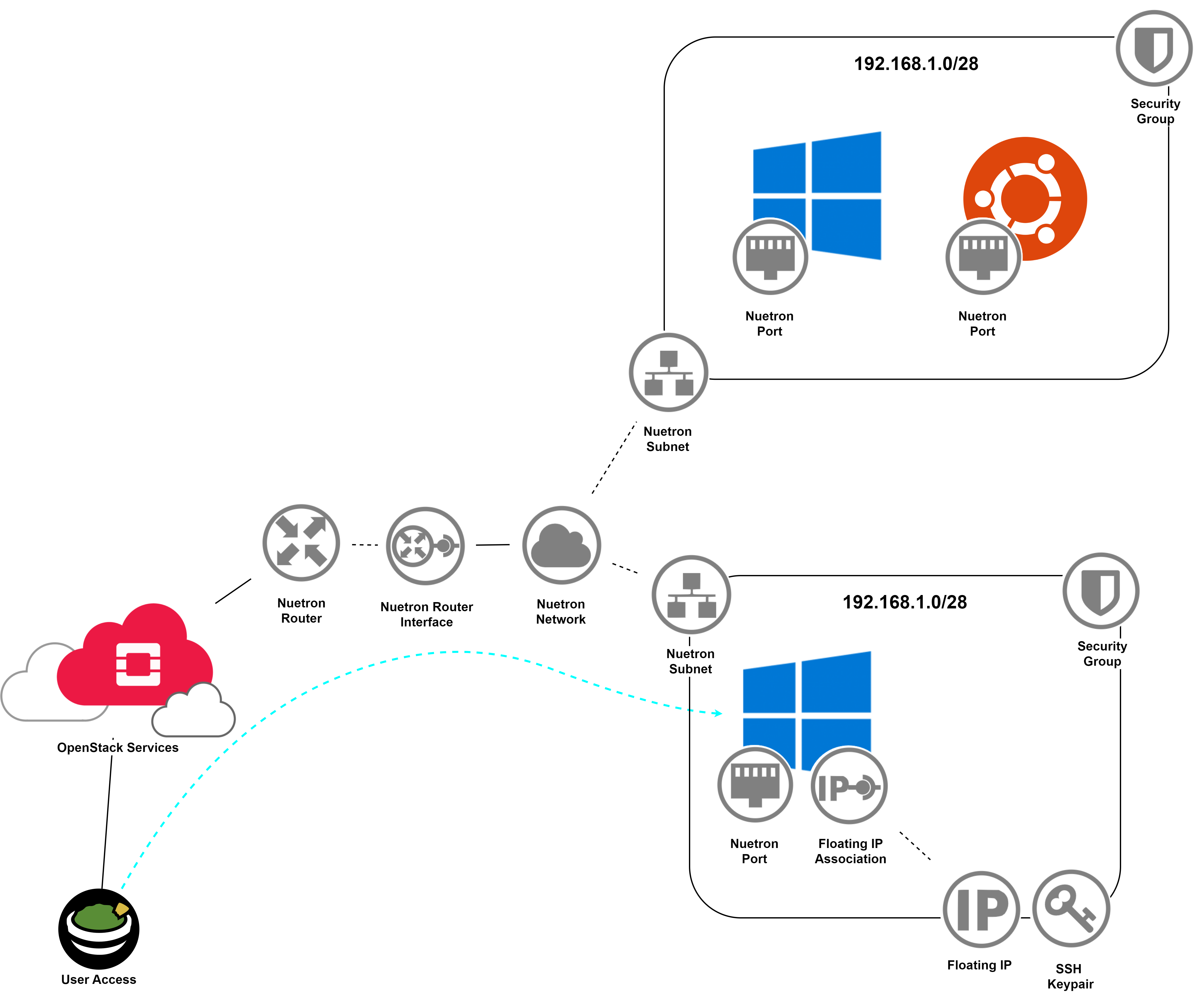
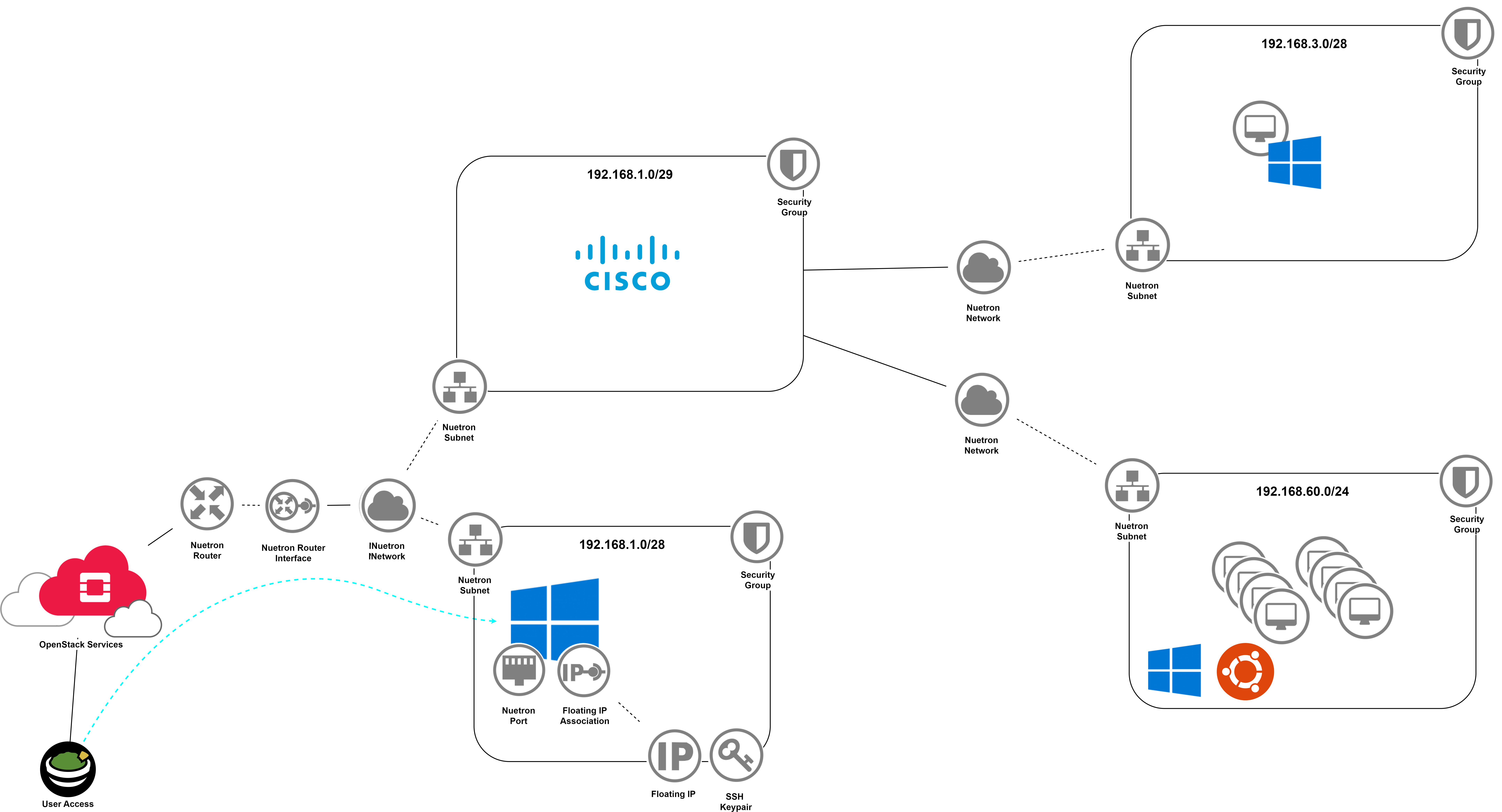
Network Diagram
Like every good network a visual representation of the networks, subnets, systems, and services that are included in the Cyber Range -
Description
A simple description stating the intended purpose of the Cyber Range -
Heat Orchestration Template
This is where we define all the resources, from the networks to the systems within those networks. We also define their characteristics, such size, Operating Systems, number of ports, etc. -
Scripts & Configuration Data
This is any and all data required to configure not only the systems, but the services that are hosted within the Cyber Range itself. This includes Active Directory, Web Services, Firewalls, Routers, Etc.